Web applications can easily become very complex. Several hundreds of thousands of lines of code (no HTML templates!) is usual at larger corporate solutions. This also means that your PHP applications follows the standards like object oriented programming, nested classes etc.
When it comes down to detect security vulnerabilities, a lot of tools are available. In a previous post I told you that we developed Chorizo! mainly because we needed a tool that checks for security vulnerabilities (both XSS issues and server side issues) very easily. I think our GUI is very nice :-)
In a previous post I introduced Morcilla to you (see video here and here and feature list here). The server side extension enable Chorizo! to have a look inside your server. Unlike other tools, you can now detect and eliminate security vulnerabilities very easily – the videos showed how to fix a local file inclusion bug within an instant.
But sometimes it’s not very easy to check if a vulnerability occured where Morcilla told you it occured. Take, for example, MySQL’s mysql_query() function. If we detect a SQL injection in the line where mysql_query happened, it may lead to irritation if you imagine the mysql_query()/pdo_query() function was called inside your SQL abstraction layer you’re using – modern applications use that. So you probably don’t know at first sight where the call was made that enabled an attacker to slip in.
In order to pinpoint this issue, it is neccessary that you get a deeper look to the callstack of all the functions that were involved calling the SQL abstraction layer. Here’s a screenshot how it looks in the upcoming version of our PHP extension:
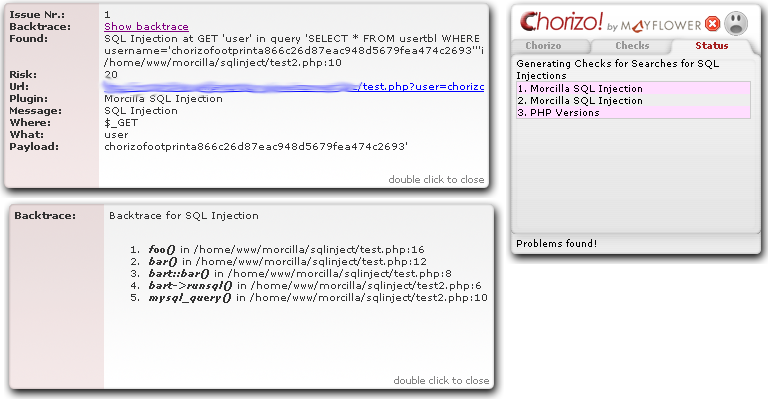
As you can see, the mysql_query() call in this example was made at /home/www/morcilla/sqlinject/test2.php on line 10. But there were previous function and class method calls that may have led to this SQL injection because they didn’t filter the input value properly.
If you’re interested which further features the PHP extension brings to you in combination with the security scanner or if you have comments and suggestions, just write us an e-mail!


Schreibe einen Kommentar